Exploration Guide

Created by Ruxe Nemico
Introduction
Exploration is a great way to make money especially for new players. It can be skilled into very easily and scales up well if you invest time and SP into it.
Many systems in New Eden have hidden sites called Cosmic Signatures. An explorer will scan the system for certain types of sites and hack the cans at the site for the loot they contain. There are several types of sites that an explorer would be interested in: Relic, Data, Covert and Sleeper.
Hacking is done via a minefield-like minigame. This minigame follows the same rules and procedures at all sites, but varies in difficulty and requires different modules to initiate. depending on the type of site.
The contents of the cans are salvage, BPCs, commodities and various items used for building or inventing advanced ships or modules.
There are quite a few topics that are beneficial, even vital to know. However, you can be successful with even basic knowledge and understanding of what's involved. We have also put a lot of work into making this guide clear and easy to use. The best way to git gud is to get out there and do it - even if you don't know everything yet. And, as always, if you have a question - never not ask.
Standing Orders
It is vital to know that there are certain systems that are off-limits for members of Brave to explore in.
If you are in Brave, please read our standing orders page before heading out to explore!
TL;DR
- Make sure you have the minimum recommended skills.
- Fly the most effective ship you can afford to lose (taking ISK you expect to make and the chance of getting killed into account).
- Research effective locations and times and the security intel involved.
- Join standing fleet and comms.
- Head out during times of minimal activity and focus on less-frequented areas, preferably in null sec.
- Always be aware of local and dscan.
- Scan from a safe, cloaked if you can.
- Launch probes in the pinpoint formation, center in 3 dimensions and scan. Re-center, lower radius and re-scan.
- Focus on getting to the opposite side of the hacking window.
- Be aware of virus strength/coherence vs hostile node strength/coherence. Don't attempt to attack if there is no need.
- Finish all sites you start if you're not in danger.
- Store loot every so often in player-owned structures.
- Sell in market hubs or contract to a buyback.
Skills
Scanning
- Astrometric Rangefinding (+5%/lvl scan probe strength)
- Astrometric Aquisition (+5/lvl scan prob duration)
- Astrometrics (+5%/lvl scan strength, -5%/lvl scan probe time, -5%/lvl scan deviation)
Hacking
- Hacking (+10/lvl Virus Coherence when hacking data sites)
- Archaeology (+10/lvl Virus Coherence when hacking relics) (Level 5 is recommended as it unlocks the Relic Analyzer II which results in fewer failed cans)
Misc
- Cloaking (Training to level 4 is recommended as this will unlock the CovOps cloak)
Ships & Fittings
You can import the fits from below to EVE by copying the text (including the [Ship, Name] part at the top), then opening the fitting window in EVE, clicking on "Browse", then "Import from Clipboard".
T1 / Low Skill
Although we originally provided fits for all factions, we now strongly suggest the Heron for T1 explo exclusively. Now anyone can fly it regardless of faction, and it's a short train.
The slot layout on the heron makes it the most recommended T1 explo frigate. Being able to fit two rangefinding arrays will make life easier for scanning with low sp characters. Alpha characters who are unable to fit a cloak can just remove it. The ship remains quite cost effective (especially considering dojo hands them out for free).
It should be noted that Sisters Core Probes can be used with any launcher including the basic one. These probes should be the first upgrade you make on your Exploratory vessel.
| Low Skill T1 Explo |
|---|
[Heron, Heron LS T1 Explo] Nanofiber Internal Structure I Nanofiber Internal Structure I 5MN Microwarpdrive I Relic Analyzer I Data Analyzer I Scan Rangefinding Array I Scan Rangefinding Array I Core Probe Launcher I, Core Scanner Probe I Improved Cloaking Device II [Empty High slot] Small Gravity Capacitor Upgrade I Small Emission Scope Sharpener I [Empty Rig slot] |
T2 / CovOps
Unless you want to scare off other explorers or want some additional safety, the T2 Exploration Frigates are the next logical steps after the T1 frigate. They offer the huge advantage of a CovOps Cloak. This cloak is an upgrade over the normal cloaks used with the T1 ships and allows you to warp while cloaked, making it very hard to catch you (Big gatecamps with bubbles are still a danger to avoid). As such, we focused on stealth and/or the ability to escape over tank. Specialization is key and it's best to focus on a fit's strengths whether based on the hull's boosts or the fit's purpose.
These fits are meant to work for the majority of players who are flying CovOps for exploration. There are upgrades you could make but they generally come at increased SP or ISK requirements. If you can run T2 Relic or Data analyzers, T2 scanning rigs or are willing to put out isk for a Sister’s Core Probe Launcher, it can boost your explo returns.
| Ninja Explo Relic Astero | Ninja Explo InstaWarp Relic Astero |
|---|---|
[Astero, Ninja Explo Relic Astero] Nanofiber Internal Structure II Inertial Stabilizers II Type-D Restrained Overdrive Injector 'Halcyon' Core Equalizer I Relic Analyzer I 5MN Microwarpdrive II Scan Rangefinding Array I Scan Rangefinding Array I Core Probe Launcher I Covert Ops Cloaking Device II Small Low Friction Nozzle Joints I Small Polycarbon Engine Housing I Small Emission Scope Sharpener I Hornet EC-300 x15 Sisters Core Scanner Probe x16 | [Astero, Ninja Explo InstaWarp Relic Astero] Nanofiber Internal Structure II Inertial Stabilizers II Damage Control II Warp Core Stabilizer II Relic Analyzer II 5MN Microwarpdrive II Scan Rangefinding Array I Cargo Scanner II Sisters Core Probe Launcher Covert Ops Cloaking Device II Small Hyperspatial Velocity Optimizer II Small Low Friction Nozzle Joints II Small Gravity Capacitor Upgrade I Hornet EC-300 x15 Sisters Core Scanner Probe x16 Nanite Repair Paste x85 |
The Astero, according to many, is the quintessential explo frigate. It is certainly one of the purposes for which CCP created it. With boosts to scanning, hacking and, of course, CovOps cloak, it's easy to see why. You can swap one of the mids (cargo scanner or a rangefinder array) with a data analyzer if you would like.
| Buzzard | Anathema |
|---|---|
[Buzzard, Buzzard CovOps Scanning Fit] Inertial Stabilizers II Micro Auxiliary Power Core II Inertial Stabilizers II 5MN Microwarpdrive II Relic Analyzer I Data Analyzer I Scan Rangefinding Array I Scan Rangefinding Array I Core Probe Launcher I Covert Ops Cloaking Device II Interdiction Nullifier I Small Gravity Capacitor Upgrade I Small Gravity Capacitor Upgrade I Sisters Core Scanner Probe x16 | [Anathema, Anathema CovOps Scanning Fit] Inertial Stabilizers II Warp Core Stabilizer II Nanofiber Internal Structure II Nanofiber Internal Structure II 5MN Microwarpdrive II Data Analyzer I Relic Analyzer I Scan Rangefinding Array I Core Probe Launcher I Covert Ops Cloaking Device II Interdiction Nullifier I Small Gravity Capacitor Upgrade I Small Gravity Capacitor Upgrade I Sisters Core Scanner Probe x16 |
| Cheetah | Helios |
|---|---|
[Cheetah, Cheetah CovOps Scanning Fit] Micro Auxiliary Power Core I Warp Core Stabilizer II Inertial Stabilizers II Inertial Stabilizers II 5MN Y-T8 Compact Microwarpdrive Data Analyzer I Relic Analyzer I Scan Rangefinding Array I Core Probe Launcher I Covert Ops Cloaking Device II Interdiction Nullifier I Small Gravity Capacitor Upgrade I Small Gravity Capacitor Upgrade I Sisters Core Scanner Probe x16 | [Helios, *Helios CovOps Scanning Fit] Inertial Stabilizers II Warp Core Stabilizer II Nanofiber Internal Structure II 5MN Microwarpdrive II Relic Analyzer I Data Analyzer I Scan Rangefinding Array I Scan Rangefinding Array I Core Probe Launcher I Covert Ops Cloaking Device II Interdiction Nullifier I Small Gravity Capacitor Upgrade I Small Emission Scope Sharpener I Hornet EC-300 x1 Sisters Core Scanner Probe x16 |
Another option when it comes to T2 frigates are Interceptors. They don't have a bonus towards exploration, but can be fit to be "insta-warp" (align time of less than 2s) and are bubble immune, so for null sec exploration they have a certain advantage. If you specialise in one type of exploration (relic or data), then you can use rigs and modules to focus on that and mitigate the lack of a hull bonus a bit. Fits again depend on your skills (especially for the align time), so you will have to find out on your own what works for you.
Interceptors that can be fit to insta-warp are the Ares, the Raptor, the Stiletto and the Crusader.
Note: Interceptors are not inherently immune to warp bubbles after the May 2021 nullification changes, they need Interdiction Nulifier module equipped. Brave Dojo has a good YouTube video on this topic Here.
T3
T3s are the most versatile ships in the game and it is this versatility that allows them to participate in exploration. Due to their subsystems they can be fit to ignore bubbles, use a covops cloak and maintain a reasonable tank and align time as well as carry refits with them.
The ship, no matter which you pick, will be the most expensive of all the exploration ships. The hull itself costs less than the Stratios, but with the subsystems and fits, you will have to spend more than half a billion ISK. It can be worth the price however, since the only downside of using a T3 cruiser for exploration is the relatively small cargohold, so you'll have to drop off your loot more often than with the Stratios, limiting your range a bit. The advantages are significant: you are very close to being uncatchable, can tank the damage of even a Superior Sleeper Cache (at least the "massive Waves" in the last room, to tank the "colssal" ones you will need more than 100k tank and very good reps) and will be able to scare away other exlporation ships, since they won't know how much DPS you can dish out (you could be combat fit after all… don't fully rely on this however, some people will call your bluff!).
When & Where to Explore
When you do exploration you can do it in any part of New Eden (taking standing orders into consideration).
Where to explore is mostly up to taste, skills & the ship you use among other things.
If you are new to exploration, try to work your way up in difficulty, so you have some funds to replace your ship when you lose it.
When you are a bit more experienced, try out new things and find your sweet spot where risk, reward and the sites you are doing all are to your liking.
Here is a link that can help you decide where to explore if you want the best isk/site ratio, but keep in mind that others are aware of this information as well, so the most lucritive places will have higher competition and camped more often than others.
https://www.reddit.com/r/Eve/comments/af7536/the_ultimate_nullsec_faction_relicdata_sites/
This link also contains data abaut where to find which T2 salvage material if you want to hunt for specific ones.
Optimal Time
The best time to explore is generally at times of low activity in a given region or system. This lowers the likelihood that you'll compete for sites and that hostiles will not be present.
Use your launcher to get a quick peek of how many people are logged in to Eve at the moment.
Dotlan (http://evemaps.dotlan.net/) can show you how active a given region and the systems contained there have been.
Region Types
HIGH SEC
High Sec offers relative safety (unless your exploration character is in Brave which is often be wardec'd), but the payouts are very low compared to the other areas of space.
while the sites in high sec are highly contested and don't pay too much, they are a good starting ground to familiarize yourself with the hacking minigame. There are also a few high sec systems that are close to null sec entries to give you easy access to better space. Be aware: these entry systems are often camped, so check dotlan/the in-game map for recent kills before you go there!
If you are already part of a player corp you may be wardec'd - which means you are actually safer in null (near your corp's space) than in high sec.
LOW SEC
Low sec has higher risk and payouts, but the absence of bubbles makes it a good starting ground. Make sure you don't warp into a smartbombing gatecamp and you should be fine.
FACTION WARFARE SPACE
Try to stay away from Faction Warfare space, since you will find more activity and many people hunting other players there. The advantages here, though, are that you are close to high sec (to get your loot to safety) and no bubbles are allowed.
NULL SEC
Null Sec has again more risk (bubbles!) and payout, but since many systems have next to no activity, once you get away from High/Low Sec you will be mostly undisturbed (unless you jump into someone's staging system). However, you must still be vigilant and check intel.
NPC NULL SPACE
if you find a good system with good connections to empty null space, this is a good option and will give you high income. However, you also have some risk (bubbles, people hunting explorers) and you are more limited to a specific area, unless you take wormholes.
WORMHOLES/J-SPACE
Wormhole Space, or J-space, also has relic and data sites. However but most of those can't be done in an explo frigate since they contain rats.
In C1, C2 and C3 wormholes you can find faction sites that are relatively safe for frigates to hack. These have the same names as the sites in normal space, with a faction name (Sansha, Guristas,…) in their name.
While sites in wormholes can give you a good payout (they are the same as Null Sec sites) you have to be very careful in Wormholes (see our section on wormholes below).
THERA
Very dangerous, but if you are dedicated and like the randomness you will have a good time. Maybe get some experience before you give it at try.
Staging
A recommended system to base your operations out of depends on a few things.
DEDICATED EXPLORATION CHARACTER
If you set up a character exclusively for exploration, you can use that to your advantage as you have more leeway to focus on what's good for this operation specifically.
- You may want to consider staging close to where you prefer explore. This way you never need to travel far to get there.
- Having a safe or convenient route from your staging system to a trading hub is a great advantage.
MULTI-USE CHARACTER
If you do not have a dedicated explo character and you have a primary staging base that is not explo-focused, we recommend 4 options:
| Corporation staging | Get into explo ship right away | Available for primary activities | May be far from optimal explo route | May be far from optimal trading hub |
|---|---|---|---|---|
| Stage close to your explo area | Get into explo ship right away | May be far from primary activities | Close to optimal explo route | May be far from optimal trading hub |
| Stage close to a market hub | May need to travel to get into explo ship | May be far from primary activities | May be far from optimal explo route | Close to optimal trading hub |
WORMHOLE TRAVEL
Another option would be to stage from wherever you want and look for wormholes that will take you to a region type of your choice. This gives you far greater range and flexibility. However, it also has a random element to it, since you don't know where you will end up, not to mention the dangers that exist in wormhole space.
Choosing a Region
The general value of loot dropped depends on the rats that inhabit a given region (In Catch & Stain, for example, you will find Sansha rats which drop the most valuable loot. In Fountain it would be Serpentis, etc.) The Sites themselves are run more or less the same.
In Wormhole Systems, you will find an entirely different type of sites (sometimes in addition to standard sites). Those have rats in them and require more than a T1 frigate to run.
In Drone Regions you won't find Relic sites. The Data Sites have loot that is completely different from all other space. While they can drop valuable Items, in general you won't find enough of them to make up for their rarity.
Planning a Route
When it comes to looking for all those sites, planning where you want to go is key to successful exploration. The systems most likely to contain viable sites are the ones that don't get visited a lot. this is because the sites spawn randomly. Choosing relatively empty systems gives you another advantage: if nobody goes there, you won't be as likely to get shot at or encounter gate camps.
In general, You should find a route with:
- No or almost no active people
- No recent kills
- Few recent jumps
A great tool for intel in this regard is Dotlan (http://evemaps.dotlan.net/)
Abiding by the above guidelines will give you the best chance for great results.
If you see that a certain route usually provides great results, you can record that route using the in-game notepad (Neocom Menu > Accessories > Notepad)
- Click the A on the left side of your client next to the current system designation
- In the search bar enter the first system & click search
- In the window that pops up, double click the correct system
- In the next window that pops up, drag the picture of the solar system into the notepad
- Repeat for the next system
- You do not need to record every system - only nodes along your path that will allow the resulting route to be recorded properly
- When you next head out - before you undock - open the notepad file (from the menu on the left of the notepad), right-click on the first system and select "Add Waypoint". Do the same for the next system in the list.
Now you need some great people on comms to talk to, a good playlist or both.
General Safety
You should go through these safety measures before you undock.
Standing Fleet
If you're exploring in our space it's a good idea to join regional standing fleet. This way if you're pointed, you may increase your chances of survival by calling out xxx's to standing.
Make sure to include your ship type and what's attacking you. A difficult thing to remember and do when you're trying to, you know, not die. However, this will increase your chances of standing responding as they are less likely to come to a confrontation with the unknown.
Comms
Just like joining standing fleet, joining the appropriate standing comms in Mumble can enable you to call for help and provide intel.
Intel Chat Channels
Sign in to the intel chat channel for the region. We have 1 currently: querious.imperium
- Look around the channel to see if a system is trouble.
- You can report neut and hostile sightings
- Drag the name from local
- Drag the system from the system name on the top left of your client
- Drag the ship type from D-scan.
- If your D-scan does not pick up the ship, put NV for No Visual
- If a lot of neuts or hostiles show up, select all in D-scan or local chat, paste in the form on the site https://dscan.me/, click submit, then copy & paste the URL to the intel chat. Remember to include the system.
Zkill
Research the system you're about to enter or a pilot who's in the system in Zkill. Zkill provides intel about combat activity in the system and by players. A recently active system or a player that you know is in the system who has a lot of kills (especially explorers) can mean that the system is still dangerous.
Dotlan
Aside from finding out how many players have been through the system, Dotlan can also tell you how many kills there have been recently. A high number of recent kills may mean there are hunters in the system.
Eve Gatecheck
http://eve-gatecheck.space/eve/
this is another useful intel tool that shows you safety intel along your selected rout. Enter the systems you will fly through, or at least the systems that will loutlne your path as you did when planning your route. this site will show you intel along the rout and provide the appropriate links to Dotlan and Zkill.
Eve Eye
https://play.google.com/store/apps/details?id=com.eveeye
https://itunes.apple.com/us/app/eveeye/id1163904317
This tool can be useful in giving you a good idea about the system you're about to jump into. You can choose from different settings like showing system security status & recent kills in system. Once it's set up by logging in and choosing options, it will follow you around so you can get a good picture of the surrounding systems at any time. It can even trace your path so you do not unintentionally explore a system twice in one run.
There is also a handy Eve Eye app for Android & iPhone because come on - how many of us have the monitor real estate of a sweet 6-screen setup.
Paranoia Levels (Vigilance)
You constantly need to have some level of vigilance regarding your environment at all times. We like to call this "Training to Paranoia".
| Space Type | Skill Level |
|---|---|
| High Sec | Train Paranoia to level 1, just to be sure |
| Low Sec | Training to Paranoia 3 or higher is a must. Watch out for other people in local, use D-scan a lot. |
| Null Sec | Paranoia 5 and Advanced Paranoia 3 are a must have. Look up people's & system's killboards on Zkill, D-scan, watch local like a hawk, don't do anything hasty (like uncloaking) without being sure you are safe. |
| Wormhole Space | Paranoia 5 and Advanced Paranoia 5 are necessary to survive. If you go there without your paranoia skills maxed out, drop off your cargo a lot, so you don't lose it all when that cloaky Proteus and his Loki friend appear next to you. |
Site Intel
In order to help you save time and enable you to help other explorers, there are tools that provide intel on the various signatures in a system.
Pathfinder
- Scan signature until you know what it is.
- Log in with Eve CREST (login).
- Find the system your in by clicking the sub-region tab (eg: East Catch) and finding the system that has your name (use CTRL-F to bring up browser search if you're having trouble).
- If the system you're in is not found right click in am empty spot and select add system.
- if feasible drag it in the correct place and link it to the correct systems.
- Otherwise leave it anywhere empty.
- Select your system by clicking on it & scroll down to the system info.
- Click Signature reader, copy the signature from your probe scanner panel (CTRL-C), paste in the form (CTRL-V) and click submit.
Scanning Down Sites
The ability to scan down sites quickly and efficiently relies on skills trained, effective probe strength and experience. Fast scanning is important: the first one to the site is entitled to the entire site, meaning no one else can start hacking cans at that site while the first pilot is doing so.
Scanning Safety
It is important to make sure you are safe while scanning. Neuts, especially hunters, can catch you unawares and destroy your ship before you have enough time to react and handle the situation effectively.
SAFE BOOKMARKS
Always scan from a safe. Safes are bookmarks you set that are not along the warp path between any 2 celestials or structures. Ideally they should also be as close as possible to being out of D-scan range of any celestials or structures. This makes an encounter with a neut or hostile much less likely.
- Find a triangle made by 3 structures or celestials. Find a spot in the middle that does not line up with the warp path between one of the triangle's points and that spot.
- Warp between 2 and leave a bookmark (CTRL-B, then submit to set) in between.
- Warp between another 2 and leave another bookmark on the other side of the triangle from the first bookmark.
- Warp between the 2 bookmarks leaving a third bookmark. This will be your safe. Delete the other 2 bookmarks.
- Instead of creating a second bookmark, you can warp from the first bookmark to another point of the triangle.
CLOAK
A cloak is an essential mod since it further decreases your chance of being detected, especially since you can no longer be scanned by combat probes. While scanning from your safe, remember to cloak up.
Train to Cloaking IV to enable you to fit a CovOps cloak which allows you to warp while cloaked.
LOCAL CHAT
Always check local to monitor for neuts. Never explore in a system with neuts unless you are experienced in handling them or escaping if you're caught
D-SCAN
Even though you'll see a neut in local if he enters the system, checking d-scan every so often can help you spot him if you miss him in local
Scanning Technique
- Launch core scanner probes in the pinpoint formation by clicking the most lower left button in the probe scanning window.
- Center the probes
- If the signature is close to a structure or celestial, center the probes over it.
- If the signature is far away from any structure or celestial, center the probes over the signature and expand the probe radius to 8AU
- Double click anywhere in space to rotate the camera 90 degrees and center again, completing the centering in all 3 dimensions.
- Scan by clicking the button in the probe scan window or by pressing B.
- It's a good idea to D-Scan at the same time by pressing V right before or after.
- Re-center, reduce the scan radius and scan again
- Continue scanning until you discover that you don't want that signature (remember to record it in Deepsafe or Pathfinder) or you get the site scanned to 100%.
- If you have trouble getting 100% you can control individual probes to further reduce the radius.
- Hold SHIFT
- Drag the probes closer to the signature individually. You will need to move 7 probes (5 around, 1 on top & 1 on bottom).
- Do not move them too close, or you will create a void pocket where no scan signal will reach.
More experienced explorers should be aware that no signature will ever spawn further than 4 AU from a celestial object, which is coincidentally the default positioning of probes when you launch them.
To utilise this, in your system map (default key is F9), in top left corner open options and deselect everything. After that you will see that there are white dots on that map, those are celestials like planets and moons. Position your probes centered on celestial that is either inside or in close proximity to Signature bubble. This will shorten your scan time for usually 2 scans.
Warping to Sites
Exploration sites are first come first serve (meaning if one explorer is already on the site you may not hack the site). Because of this, it's important that you warp to the site as quickly as you can to beat other explorers who may be after that site.
If you suspect the site may be camped, warp cloaked to a significant distance to avoid detection and observe the situation.
As an added safety feature you can drop a cheap piece of cargo (like carbon. Yes - there's actually a use for carbon) at the warp-in. This will cause any cloaked ship warping to 0 to decloak as soon as it lands, potentially buying you precious seconds.
Types of Cans in a Site
There are a few different kinds of 'cans' in the site. In order of increasing value, they are :
| Relic | Data |
|---|---|
| Rubble | Com Towers |
| Remains | Mainframe |
| Ruins | Databank |
It's important to realize that cans of generally lesser value can still hold a jackpot in this specific instance. they therefore should not be ignored. (We have all experienced the "single carbon Ruins/Databank" and the "dank IAP Rubble/Com Tower".)
Hacking Cans
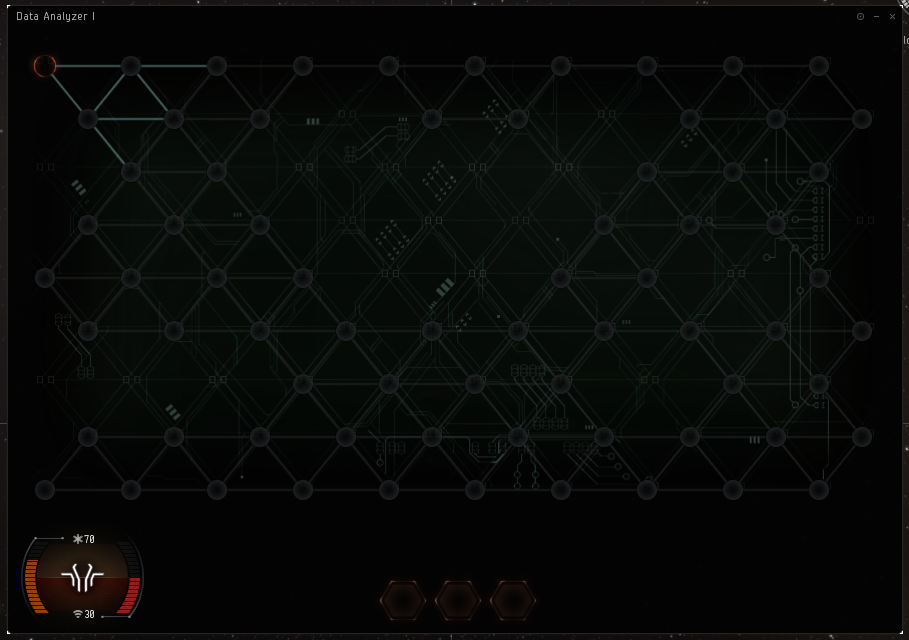
Guiding your virus through a containers security system can be challenging, but also fun. Imagine futuristic Windows Minefield on steroids.
Hacking Safety
Remember to check local chat and D-scan every so often
Hacking Technique
On activating the appropriate module on the can, the hacking interface will come up.
At the bottom left is your hacking virus status. The bottom number & the meter to the right is your virus strength - the amount of damage you do with each click on a hostile node or system core. The top number & the meter on the left is your coherence (health). This can be hurt by hostile nodes & the system core.
Your starting point is the empty orange circle - shown here on the top left. You can proceed by clicking on empty green nodes that are adjacent to your starting point & the ones you've already selected.
 As you click on nodes, you'll see a number in the node ranging from 5 to 1. The lower the number, the closer you are to a utility subsystem, data cache or the system core.
As you click on nodes, you'll see a number in the node ranging from 5 to 1. The lower the number, the closer you are to a utility subsystem, data cache or the system core.
In each hack, you will encounter several types of hostile nodes, helpful tools, and the system core which is your goal. The health and damage on those nodes are represented just as your own stats are.
SYSTEM CORE
All of the Core nodes function in the same way, with an increasing health as the difficulty of the hack increases. These are the nodes found in the sites.
HOSTILE NODES
UTILITY SUBSYSTEMS
The following hacking tools, and how you use them, can make or break a hack. The tools will show up when you uncover a node on the grid, and once you click that same node they will be added to your utility toolbar (the row of slots in the bottom of the above image of the hacking interface). To activate one of the tools, simply click on it.
DATA CACHES
SYSTEM CORE LOCATION
The system core can be anywhere - but there is still some logic behind it. If your starting point is in the corner of the hacking window, System Core will never be closer than 8 nodes from your starting point. Which can speed your hack immensely because it allows you to skip entire regions that are trying to bait you. However, if you spawn in the middle, there is no logic used, the core can be anywhere.
THE RULE OF 6
Ah yes, the famous rule of 6 you keep hearing about. Here's the rundown:
You will sometimes find a node surrounded by 6 other nodes (as can be seen in the hacking interface above among the as-of-yet unavailable nodes). It is very likely, though by no means guaranteed that the center node is safe. You may even find a path made by nodes surrounded by 6 other nodes that provide you (probably) safe passage to where you want to go in the hack. If you do encounter a defensive subsystem in a center node (like a firewall), then the system core will always be adjacent to that subsystem.
A small side note, if you ever encounter Secondary Vector Utility, it means you have a Virus Suppressor somewhere. Try to save it for that nasty thing.
It should also be mentioned that, after using Secondary Vector Utility you don't have to click on that node second or third time for it to apply damage. You can simply click on other nodes.
Failing a Can
It happens - even with dank skills.
Each can allows for 2 opportunities to hack it, with the exception of ghost site cans.
It is a good idea to set your hacking mod auto-repeat to off (right click > Auto-Repeat Off). Once set, the mod will only cycle once, which is enough to get the hack going, then shut down. This allows you to start the mod again for the second hack right away instead of needing to wait for a cycle to complete.
If you fail a can twice it will explode. This normally does no damage to you, however in the case of ghost sites the can will explode after one fail and deal enough damage to instantly destroy most explorers, so be careful!
Loot
Looting the Can
After successfully completing the hack you can loot the can as you would any other container because otherwise why did you even, bruh?
Loot Types
There are 3 primary types of exploration loot: T1, T2 & Datacores. Datacores can be looted from data sites while T2 loot can be looted from relics. T1 is identified by an orange or yellow background, while T2 loot is identified by a blue background. Datacores are identified by a circle with a line of light against a digital background. T2 is generally worth more. You may also pick up other types of salvage - some worth little while other worth a lot such as faction BPCs.
Due to the high-m3 / lower-ISK nature of data site loot, it is often worthwhile to skip them altogether. This allows you to get to potential relic sites sooner and to slow down competing explorers who waste their time on data sites. The exceptions are the various sleeper sites, since the data aspect is mostly the hack that opens the site in the first place, allowing access to the relics within.
Loot Safety
We all get blown up some time or another (if you're doing Eve right, that is). Why risk that happening to a boatload of loot?
It is advisable to drop your loot off every so often so if you are killed, most of your loot is safe and retrievable.
Loot should be kept in friendly-player-owned structures such as citadels. It should not be stored in stations. The reason is as follows: If a player-owned structure is destroyed, your loot will be placed in asset safety. Stations, while not able to be destroyed, can be taken over by hostiles. Your loot will therefore not be placed in asset safety, but will remain locked in a station that you can't dock in. Read more about asset safety here: https://support.eveonline.com/hc/en-us/articles/208289365-Asset-Safety.
The threshold for the amount of loot that needs to be stored is up to each explorer. You need to think about & decide how much loot you feel comfortable taking along with you. That includes considering how great the risk of losing it is & the inconvenience of going back and picking up all your loot in various locations. A generalized rule of thumb is double the cost of your fitted ship, but you need to do what's comfortable for you. As you gain more experience, you may feel comfortable scaling back the number of times you deposit loot and even strategically set specific stations along your route as hubs for convenience in travelling.
Selling Loot
You can contract your loot to one of the buybacks we feature. Although they buy at a percentage of Jita buy, you are essentially paying a little for convenience and the ability to avoid market trading activities if you do not enjoy that. Learn more and find buybacks at Buyback Programs.
If you do like to have fun with spreadsheets and economic charts for some reason, you can ship your loot to markets like Amarr and Jita and manage orders. Learn more and find freight services at Hauling Programs.
Site Respawn
When a site is finished, another is spawned. There is debate as to what area the site respawns in and what type of site it is. The only known fact about respawns is that if finished, it respawns almost immediately. If, however, it is not finished, it takes time to respawn, possibly half an hour.
Due to respawn mechanics, we strongly request that all explorers finish any sites they start. Once you hack the first can, you are responsible to finish the site unless you are in danger. If you are scanning the cans before hacking, fail any worthless cans until they self-destruct. This enables as many sites as possible to be available to fellow explorers at all times. If you do not finish sites we will hunt you down. Just kidding. Maybe.
There is one exception to this rule. If you are doing the site just before dt (meaning you have the 5 minutes server shotdown timer on your screen) and you leave at least 1 can up (preferably the least valuable one) and you stay in the site. When you log back in after dt the site respawns with all cans. (Keep in mind that sites do not respawn immidiatly after dt generally speaking. It takes something like 5-10 minutes.) So basically you can hack and loot them again. It's not worth to build your exploration methods/timing around this trick, but it's quite good if you randomly happens to hack around dt.
Special Sites
Covert Facilities / Ghost sites
Some data sites will turn out to be covert facilities (also called ghost sites). If a data site has 4 cans it's a ghost site. It's usually 3 with the same name and the 4. with a different one which is a harder hack with higher chance of more valuable loot.
When you land at these sites, a timer with a random duration will start. (If you use covert cloak and arrived in cloak, the timer starts when you decloak.) The timer is not displayed. If you fail a hack the cans explode for a massive damage. If you try to warp out during the hacking minigame, the can you are hacking automatically fails and explodes dealing damage. When the timer ends, rats will warp in, destroy all the cans and defend the site. The rats use warp disruption. They do not drop loot nor are they worth anything in terms of bounties, but they deal a lot of damage.
The damage dealt whenever any can explodes, whether due to can failure or the timer running out, is massive. Any frigate will be destroyed. It is possible to fit a stratios or a t3c full of buffer tank to survive the explosion.
These sites are high risk high reward encounters. The loots are valuable, but you will have no time to open all cans (alone). One good way to do these sites are in t1 exploration ship (so you do not lose much in case of a failure) fitted entirely for completing the hacking minigame and leaving after 1 or 2 opened cans.
Sleeper Cache Sites
These sites come in three flavors. Limited, Standard and Superior. The hacking remains the same in each of these caches. The main difference are the step required to safely run these sites. This added difficulty also increases the reward.
LIMITED
After you scan out the site, you will warp to the first room. Here you will see a can and an acceleration gate. Hack the can. (if you fail this hack, a 2 minute timer will start, after which the can will explode)
The second room is where things get difficult. You start by hacking the Remote Pressure Stabilizer to the right. Right after you hack this can, you'll need to rush over to the Dented Storage Depot. You will only have 2-3 minutes to hack the can. After you do, immediately return to the warp in beacon or you'll get hit by the gas cloud.
The next step is to hack the Remote Defense Grid Unit. After you hack this can, you will have free access to the rest of the cans. You will need to watch out for the gas clouds and avoid those areas. Hack the remaining cans and enjoy the spoils!
Wormholes
Wormholes, dangerous and mysterious as they are, can provide quite a profitable and adventurous experience. At the very least, when done properly, it can add an extra system to explore along your route.
Wormhole Intel
There are tools available to provide some measure of intel with regard to wormholes. If you do scan down a wormhole, please report it whether you plan on entering it or not.
PATHFINDER
- Apply as you would any other signature
- Once you enter the wormhole, you can apply the system designation by clicking on "unassigned" in the signature line item under the system column and choosing the system from the dropdown.
Wormhole Safety
Wormhole space, or J-space, is more dangerous than null due to the difference in how local works. In J-space pilots do not show up on local chat unless they chat while you're there. Needless to say it's far easier for someone to sneak up on you & kill you before you even realize what is happening.
D-scan is therefore your best friend, as are a heightened awareness and greater adherence to proactive safety measures. In addition, some exploration sites have rats, some of which will be too difficult for a single pilot to defeat.
J-space also does not have gates. An entrance/exit is not readily available on your overview.
The following safety guidelines can help you survive and even come to enjoy exploration in wormhole space and the rewards it can offer.
- Bookmark (CTRL-B) your entrance wormhole the second you enter. Otherwise you'll need to scan down and check each wormhole in the system to find the correct one when you want to leave.
- Train both Paranoia & Advanced Paranoia to V. In other words - be extremely vigilant.
- D-scan D-scan D-scan. Then D-scan some more. Although probably annoying at first, the lack of intel from local makes constant, repeated use of D-scan vital.
- Cloak is a must. Preferably CovOps cloak.
- So is making a safe right away. Because what good is cloak if a tengu decloaks you by landing right next to you.
- If you see ships or probes on D-scan and you are not prepared for a powerful confrontation, GET OUT.
Wormhole Exploration
Exploration in wormholes works much the same way as it does in J-space.
Wormhole exploration is recommended for advanced users only. This is due to the danger wormhole space (or J-space) poses and the experience and skills needed to safely & effectively use that space.
If you are not prepared to kill rats (some really strong) you should only do the faction sites. Those are the sites with one of the rat types in the name (like Sansha or Guerista). The other sites have rats that may melt your face.
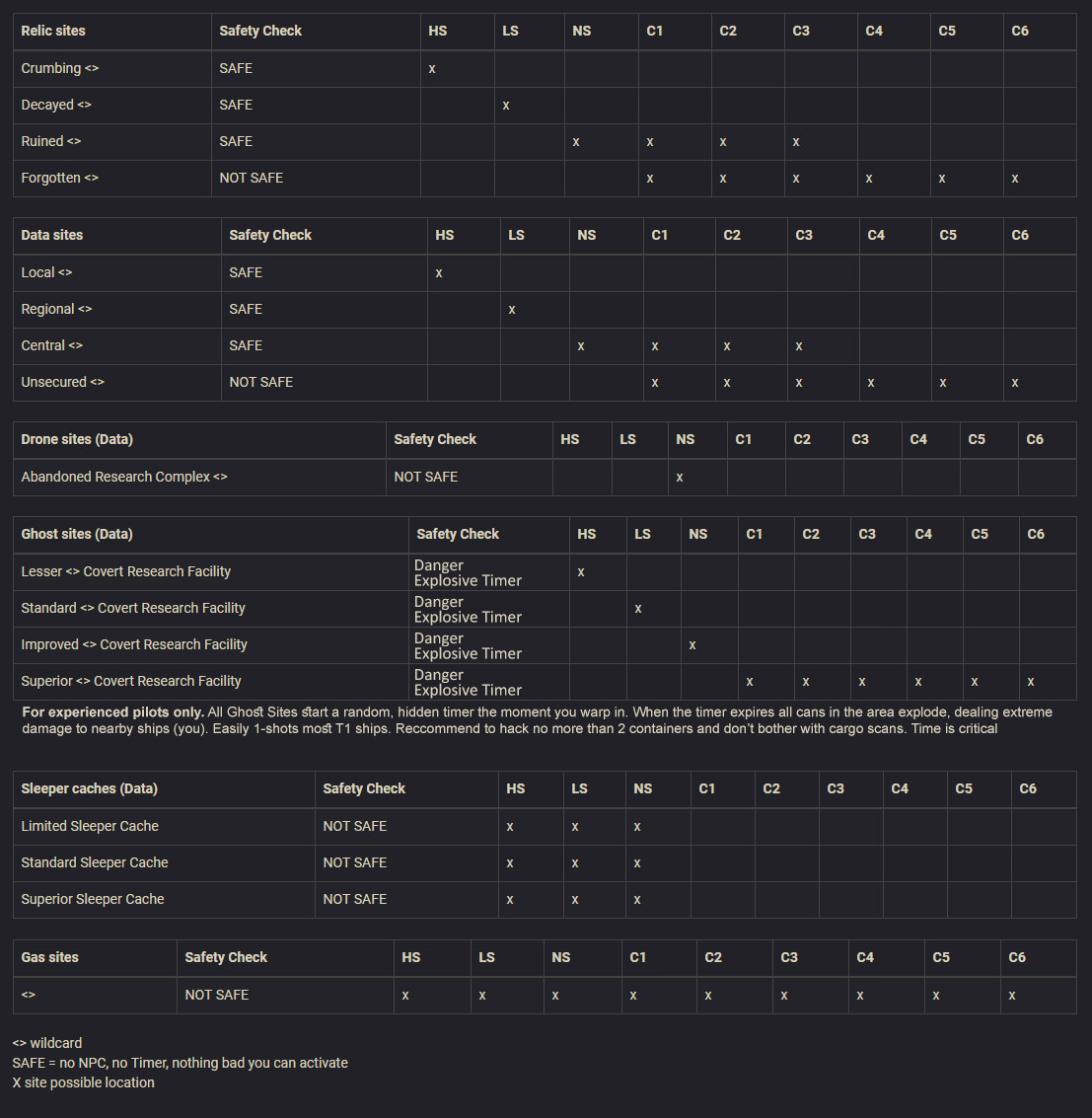
Site Safety Check Cheat Sheet
A quick cheat sheet for evaluating site danger based on the location name. Location name can be seen once the site is scanned at least 75%. This chart was borrowed and adapted from an article on Eve-Scout Forums
Related Activities
combat explo, selling sites, probing for fleets…